A detailed survey of denial of service for IoT and multimedia systems: Past, present and futuristic development | SpringerLink

Botnet attack detection in Internet of Things devices over cloud environment via machine learning - Waqas - 2022 - Concurrency and Computation: Practice and Experience - Wiley Online Library
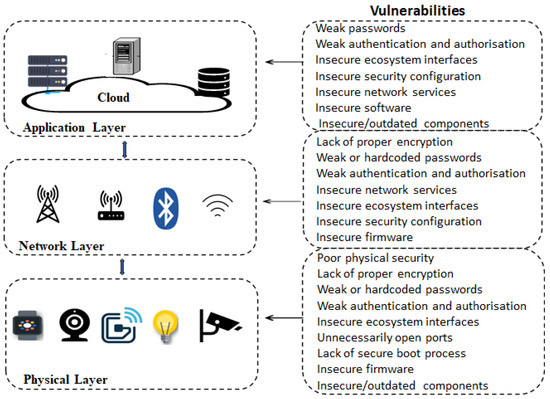
Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks




![TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube TUTO] Comment trouver l'ip de quelqu'un sur skype et le BOOT (DDOS) - YouTube](https://i.ytimg.com/vi/iwYldG8VYsY/maxresdefault.jpg)